Defensive Coding
and Hardened JavaScript
- built for DEFCON31,
- updated for NodeConfEU, Confidence, X33fcon
- and now JSNation!
by @naugtur
Who's that guy?

https://naugtur.pl
 Wouldn't it be great to fearlessly use them like we did back in 2015?
Wouldn't it be great to fearlessly use them like we did back in 2015?
 What if a package turns malicious?
What if a package turns malicious?
exfiltration
fetch, process.env
prototype pollution
RCE
fs
event-stream

process
window
Lambda function
ClFl worker
iframe
thread
process
process
process
📦
📦
ClFl worker
iframe
thread
process
process
process
📢
👂
worker
isolate
thread
process
process
process
Let's install some dependencies!
Ok, catch this: 📦
I'm not runing that.
That's what you think.
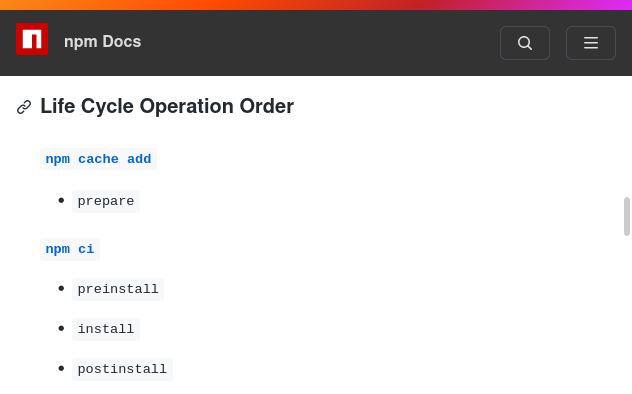
"postinstall": "echo 💩 > /etc/hosts"
Hold my 🍺
├─app.ts
├─node_modules
│ ├─@naugtur
│ │ └─evilpackage
| │ ├─evilPlots.js --,
| │ └─package.json |
│ └─typescript 💩
│ ├─lib |
│ | └─tsc.js <-------'
│ └─package.json
└─package.json
And in that moment
the installation process was protected
(Or find a common hallucination to [slopsquat](https://socket.dev/blog/slopsquatting-how-ai-hallucinations-are-fueling-a-new-class-of-supply-chain-attacks))
I could help you set up LavaMoat in your project
@naugtur naugtur.pl
@naugtur naugtur.pl